Information of TeslaCrypt
TeslaCrypt is a new ransom virus similar to Cryptowall or Cryptolocker.Usually this kind of virus can infiltrate into the computer through spam email attachment, malicious links or hacked sites, etc. Once gets into the computer, TeslaCrypt will change the computer setting including the system files and registry entries. It can run automatically at the background without any consent. It can encrypt the files on the compromise computer and ask the victims to pay money to get the decrypted key.
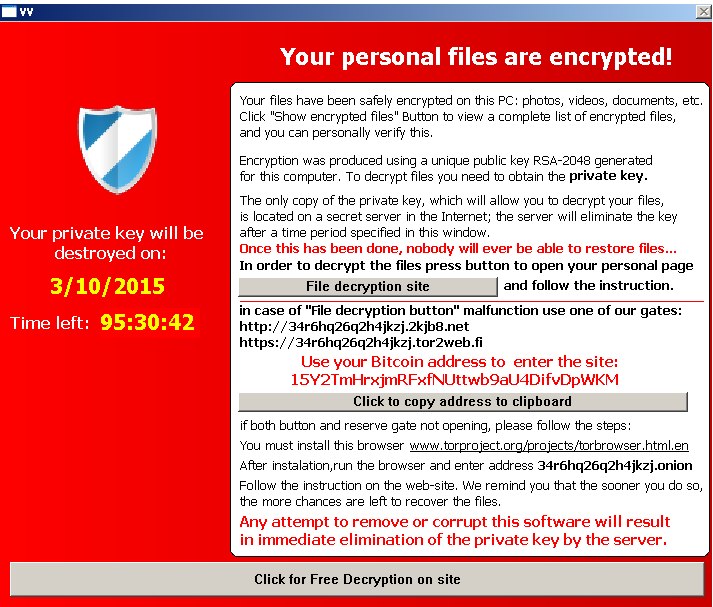
TeslaCrypt will create a file called: HELP_TO_DECRYPT_YOUR_FILES.txt to show the instruction to get the key to recover your file. TeslaCrypt accepts payments from PayPal My Cash with the ransom of $ 1000, or $ 500 by bitcoin.
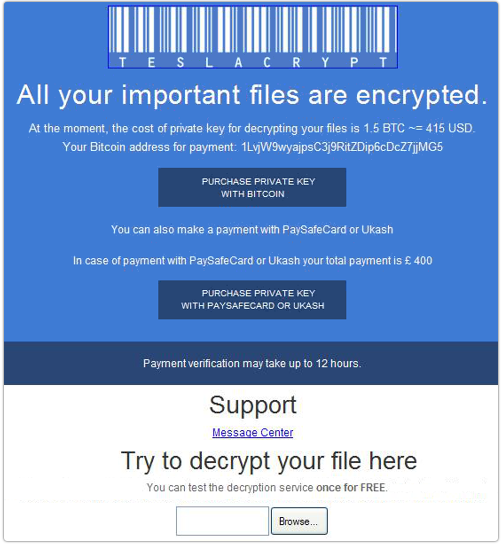
However, it is no guarantee.It is not suggested to pay for the ransom. There seems to be some labs or online services which allow infected users to retrieve their private key by uploading a sample file, and then receive a decryption tool. But most of the experts states that the only method you have of restoring your files is from a backup or Shadow Volume Copies if you have System Restore enabled. It is suggested to remove TeslaCrypt immediately to prevent further damage. And it is recommended to keep a powerful and well-known antivirus program like Spyhunter to protect your computer.

TeslaCrypt will create a file called: HELP_TO_DECRYPT_YOUR_FILES.txt to show the instruction to get the key to recover your file. TeslaCrypt accepts payments from PayPal My Cash with the ransom of $ 1000, or $ 500 by bitcoin.

However, it is no guarantee.It is not suggested to pay for the ransom. There seems to be some labs or online services which allow infected users to retrieve their private key by uploading a sample file, and then receive a decryption tool. But most of the experts states that the only method you have of restoring your files is from a backup or Shadow Volume Copies if you have System Restore enabled. It is suggested to remove TeslaCrypt immediately to prevent further damage. And it is recommended to keep a powerful and well-known antivirus program like Spyhunter to protect your computer.
Instrcution to remove TeslaCrypt
Method 1: Manual removal
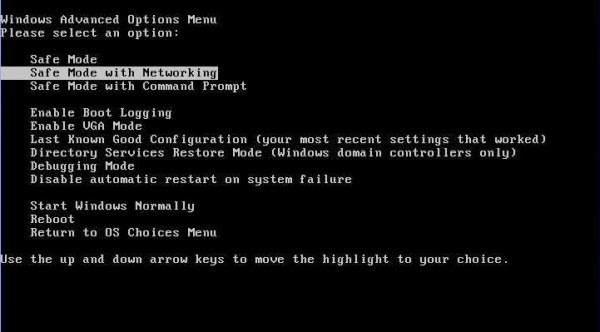
Boot up the infected computer, press F8 at the very beginning, choose “Safe Mode with Networking” and press Enter to get in safe mode with networking.

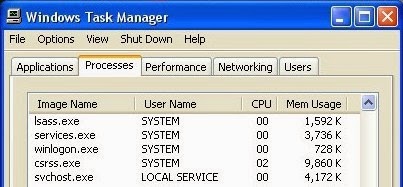
Step 1: Press CTRL+ALT+DEL or CTRL+SHIFT+ESC to open Windows Task Manager and close all the related running processes.
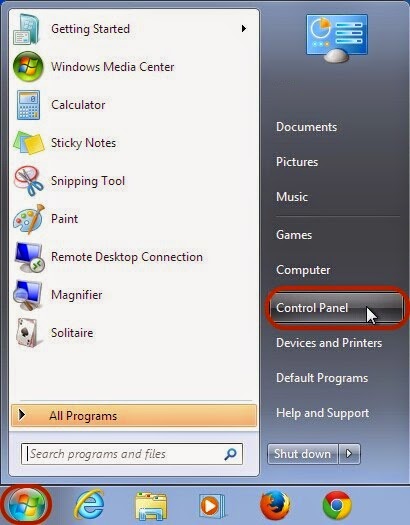

Step 2: Remove TeslaCrypt from control panel.
1) On the Start menu (for Windows 8, right-click the screen's bottom-left corner), click Control Panel.

Windows Vista/7/8: Click Uninstall a Program.
Windows XP: Click Add or Remove Programs.
2) When you find the program TeslaCrypt, click it, and then do one of the following:
Windows Vista/7/8: Click Uninstall.
Windows XP: Click the Remove or Change/Remove tab (to the right of the program).
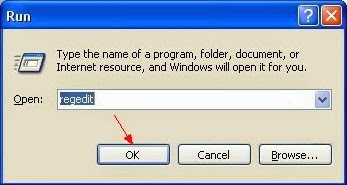
Step 3 Go to the Registry Editor and remove all the infection registry entries listed here:
(Steps: Hit Win+R keys and then type regedit in Run box to search)
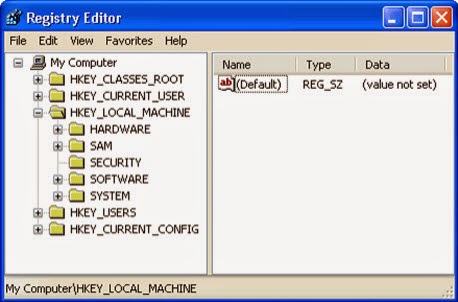
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
Method 2: Automatic Removal with SpyHunter
SpyHunter is a world-famous real-time malware protection and removal tool, which is designed to detect , remove and protect your PC from the latest malware attacks, such as Trojans, worms, rootkits, rogue viruses, browser hijacker, ransomware, adware, key-loggers, and so forth.
Boot up the infected computer, press F8 at the very beginning, choose “Safe Mode with Networking” and press Enter to get in safe mode with networking.

Boot up the infected computer, press F8 at the very beginning, choose “Safe Mode with Networking” and press Enter to get in safe mode with networking.

Step 1: Press the following button to download SpyHunter.
Step 2: InstallSpyHunter on your computer.
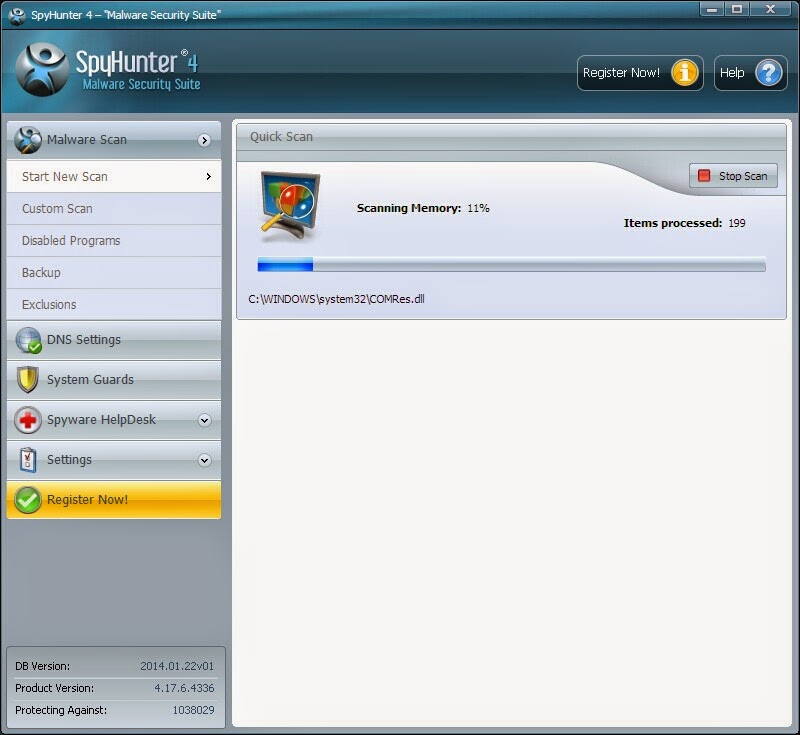
Step 3: Scan computer now!



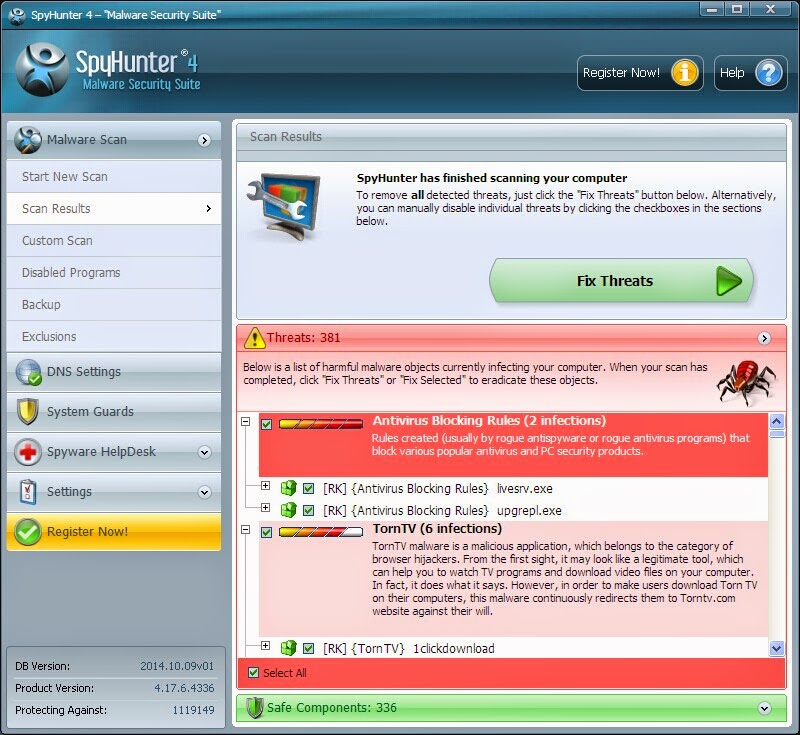
Step 4: Select all and then Remove to delete all threats.
Note: Manual removal is very difficult. If you don’t have sufficient expertise in dealing with the manual removal, it is suggested to Install Spyhunter to remove viruses safely and quickly.


No comments:
Post a Comment