Damages caused by Exploit:Java/CVE-2010-4452
Exploit:Java/CVE-2010-4452 which is able to attack computers with Windows operating systems is a pesky Trojan horse that newly designed by cyber criminals to damage the infected system severely from many aspects. The most harmful function of Exploit:Java/CVE-2010-4452 is the ability that helps cyber hackers connect to the infected computer remotely without users’ approval. Your privacy saved on the machine may be put at risk after the infiltration of Exploit:Java/CVE-2010-4452.
Your computer will result in poor performance after the appearing of Exploit:Java/CVE-2010-4452. Windows freeze up while loading web pages, common applications run improperly during your online activities, system suddenly crashes down with blue or black screen of death, as time goes on, more and more PC issues may also arouse by Exploit:Java/CVE-2010-4452 one after another.
What's worse, Exploit:Java/CVE-2010-4452 causes virtual security risks by chiseling up some back doors in the background. Other types of PC threats like spyware, malware, and worms may easily invade into the compromised PC via these loopholes. In a word, Exploit:Java/CVE-2010-4452 is a harmful PC threat which should be removed from your browser as soon as possible. You can follow the guide below to continue. It is suggested to scan your computer with a powerful antivirus program like Spyhunter to check out the problem and remove viruses.
Best Way to Remove Exploit:Java/CVE-2010-4452 Completely
Solution one: Manually Get Rid of Exploit:Java/CVE-2010-4452
Solution Two: Remove Exploit:Java/CVE-2010-4452 with Spyhunter Anti-Spyware Software
Solution one: Manually Get Rid of Exploit:Java/CVE-2010-4452
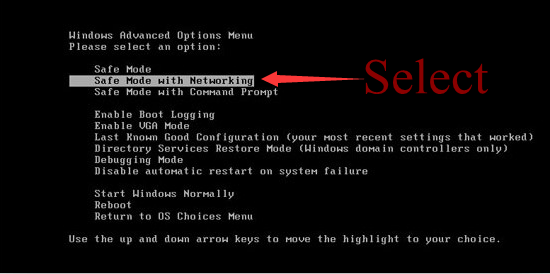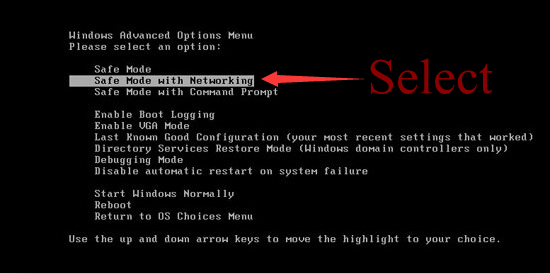
Step one: Get into the safe mode with networking
To perform this procedure, please restart your computer and keep pressing F8 key until Windows Advanced Options menu shows up, then using arrow key to select “Safe Mode with Networking” from the list and press ENTER to get into that mode.

Windows 7/Vista
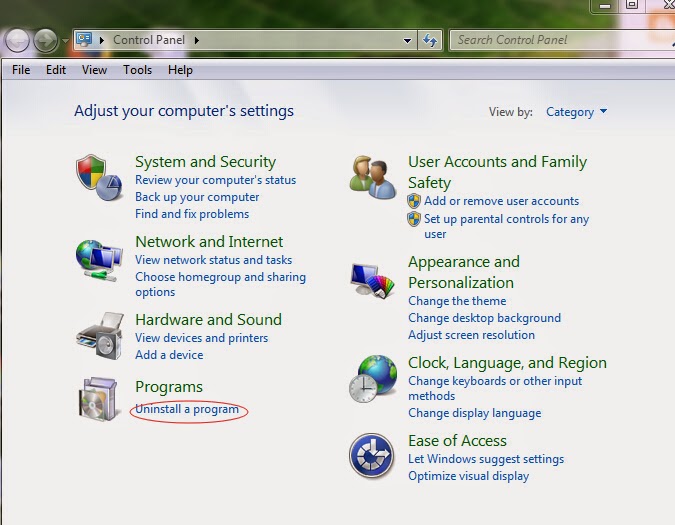
(1) Go to Start, and then click the Control Panel.
(2) Select Uninstall a Program.
(3) Find Exploit:Java/CVE-2010-4452 related programs and then click on Uninstall.
03WE63~Y%24YT_IVBBXDY.jpg)
Windows XP
(1) Go to Start, choose Settings and then click on Control Panel button.
(2) Click on Add or Remove Programs.
(3) Select Programs and Features.
(4) Find Exploit:Java/CVE-2010-4452 related programs and then remove them.
Window 8
(1) Move the mouse cursor to the bottom right corner of the screen.
(2) Click Settings on Charms bar and go to Control Panel.
(3)Select Uninstall a program and remove Exploit:Java/CVE-2010-4452 related programs.
Step Three: Show all hidden files and clean all the malicious files about Exploit:Java/CVE-2010-4452 .
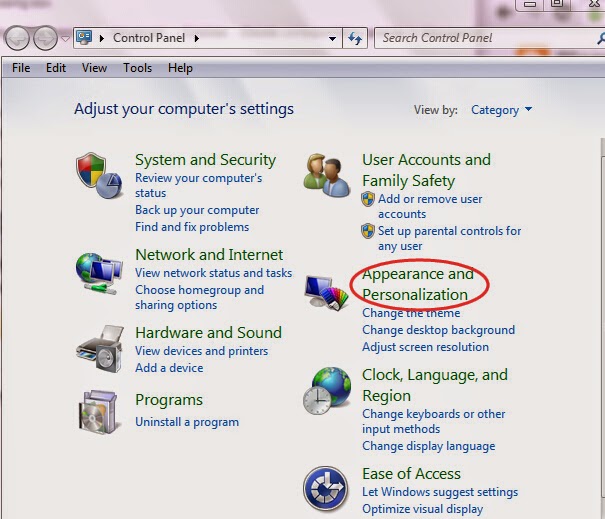
(1) Click the Start button and choose Control Panel.
(2) Clicking Appearance and Personalization, and then find Folder Options then double-click on it.
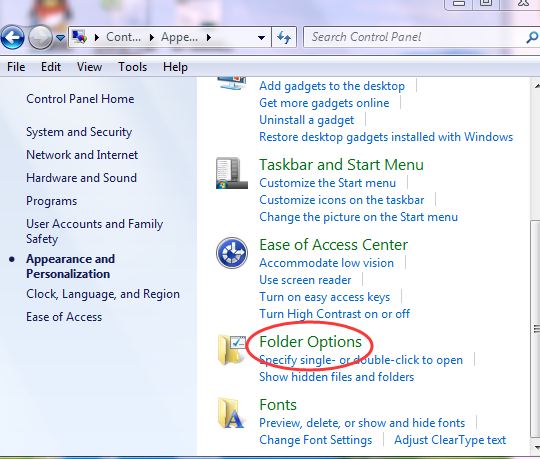C(3%24H8US44Q)I45.png)
(3) In the pop-up dialog box, click the View tab and uncheck Hide protected operating system files.
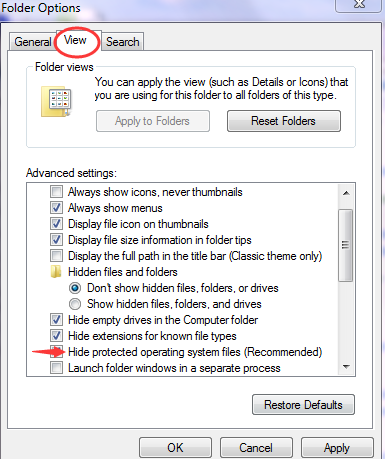
(4) Click OK and then delete all the harmful files created by Exploit:Java/CVE-2010-4452 .
%AppData%\<random>.exe
%CommonAppData%\<random>.exe
C:\Windows\Temp\<random>.exe
C:\Program Files\<random>
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = "%AppData%\<random>.exe"
HKLM\SOFTWARE\Classes\AppID\<random>.exe
(Sometimes Exploit:Java/CVE-2010-4452 damage different systems via dropping different files and entries. If you can’t figure out the target files to delete or run into any other puzzle that blocks your manual removal process, you could get a professional removal tool to kick Exploit:Java/CVE-2010-4452 ’s ass quickly and safely.)
Solution Two: Use SpyHunter to remove Exploit:Java/CVE-2010-4452 completely
SpyHunter is an adaptive antimalware detection and removal tool that provides rigorous defence against the newest threats including adware, malware, trojans, rootkits, bootkits and malicious software. SpyHunter's most advantageous feature is the free of charge Spyware HelpDesk, which can generate specific custom fixes for your unique problem.
Step 1. Click the icon below to download Spyhunter antivirus program.
Step 2. Next, you should follow steps to get Spyhunter installed into your computer.
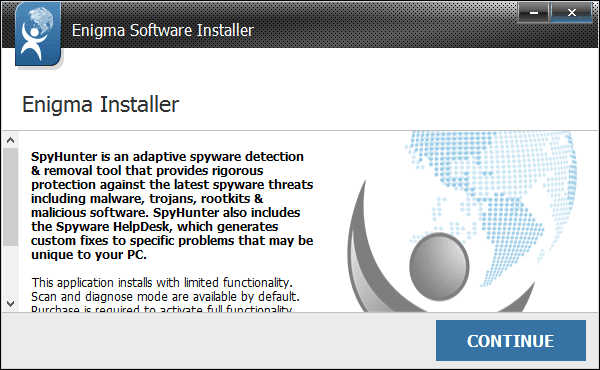
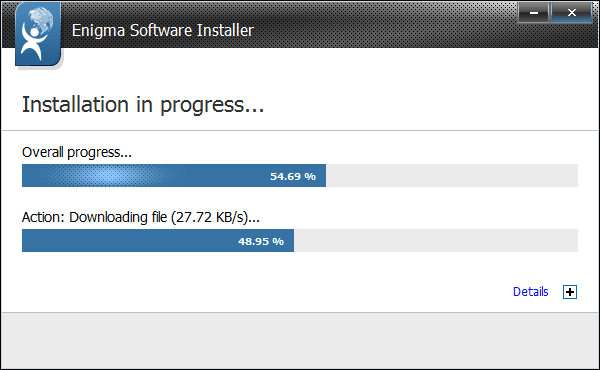

Step 3. After Spyhunter get installed, you just need to scan your computer to find out these threats.
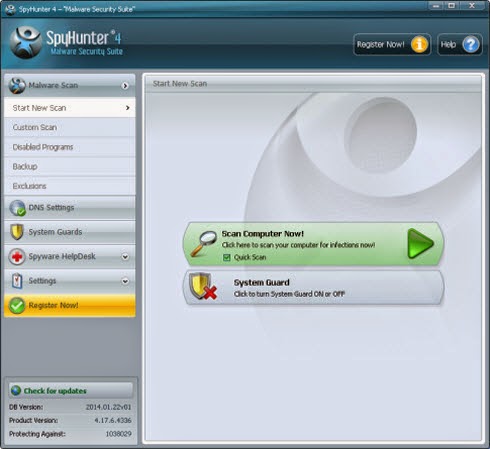
Step 4. Basically, anything if it is harmful or suspicious will be detected, and Spyhunter can help you take care of everything as long as you click the remove button.
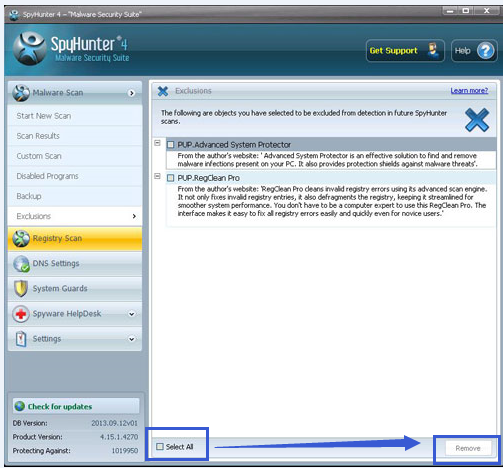
Step 5. Just for making sure all threats are fully cleaned up, you are suggested to reboot your machine to give it a second check.
Note: If you haven’t sufficient PC expertise and don’t want to make things worse, to remove Exploit:Java/CVE-2010-4452 safely and permanently, it is recommended to download SpyHunter to clean up the infection in a few minutes without repeating. Hurry up to drag all the PC bugs away from your computer forever!


No comments:
Post a Comment